Метод 2: отключение безопасности на основе виртуализации
Если вы следовали приведенным выше инструкциям и уже подтвердили, что на самом деле не имеете дело с конфликтом между Hyper-V и Vmware, возможно, вы видите значок «VMware и DeviceCredential Guard несовместимы”Ошибка из-за того, что на вашем компьютере установлена Безопасность на основе виртуализации -Это требуется для некоторых типов виртуальных машин.
Эта безопасность на основе виртуализации обеспечивается с помощью политик Редактор локальной групповой политики. Но имейте в виду, что по умолчанию эта утилита доступна только для Windows 10 PRO и более старых версий PRO.
Примечание: Если у вас домашняя версия, вы можете вручную установить утилиту gpedit в Windows 10 Home.
Если Редактор локальной групповой политики (gpedit) доступен в вашей версии Windows, и вы хотите развернуть это возможное исправление, следуйте инструкциям ниже (вспомогательное руководство A), чтобы отключить безопасность на основе виртуализации в специальной политике viit.
Если вы используете домашнюю версию и не хотите загружать неопубликованный редактор локальной групповой политики, следуйте второму руководству. (вспомогательное руководство B) для отключения безопасности на основе виртуализации viRegistry Editor.
A. Отключить безопасность на основе виртуализации viGpedit
-
Нажмите Клавиша Windows + R, чтобы открыть диалоговое окно «Выполнить». Затем введите ‘Gpedit.msc’ внутри текстового поля и нажмите Входить открыть Редактор локальной групповой политики.
Запуск редактора локальной групповой политики
Примечание: Когда вам будет предложено UAC (Контроль учетных записей пользователей) окно, нажмите на да чтобы предоставить доступ администратора.
-
Как только вы окажетесь внутри Редактор локальной групповой политики, перейдите в следующее место, используя меню слева:
Конфигурация компьютера — Административные шаблоны — Система — Device Guard
- После того, как вы доберетесь до этого места, перейдите в меню с правой стороны и дважды щелкните Включите безопасность на основе виртуализации.
Включение безопасности на основе виртуализации - Как только вы окажетесь в меню настроек Включите безопасность на основе виртуализации политики, установите переключатель в положение Отключено и нажмите ОК чтобы сохранить изменения.
- После включения этой безопасности перезагрузите компьютер и посмотрите, будет ли проблема решена при следующем запуске компьютера.
Б. Отключение безопасности на основе виртуализации viRegistry Editor
-
Нажмите Клавиша Windows + R открыться Запустить чат. Внутри текстового поля введите «regedit ’ и нажмите Входить открыть Редактор реестра. По запросу UAC (Контроль учетных записей пользователей)нажмите да чтобы предоставить доступ администратора.
Запуск редактора реестра
-
Как только вы войдете в редактор реестра, используйте левое меню, чтобы перейти к следующему месту:
HKEY_LOCAL_MACHINE \ System \ CurrentControlSet \ Control \ DeviceGuard
Примечание: Вы можете перемещаться сюда вручную или вставить местоположение прямо в панель навигации и нажать Входить чтобы попасть туда мгновенно.
- После того, как вы окажетесь в правильном месте, перейдите в правую секцию, щелкните правой кнопкой мыши пустое место и выберите Создать> значение DWORD (32 бита) из появившегося контекстного меню.
Создание нового значения DWORD (32) бит -
Назовите вновь созданный DWORD EnableVirtualizationBasedSecurity, затем дважды щелкните по нему и установите База к Шестнадцатеричный и ценность чтобы отключить безопасность на основе виртуализации.
Настройка значения EnableVirtualizationBasedSecurity
- Ударить ОК чтобы сохранить изменения, закройте редактор реестра и перезагрузите компьютер, чтобы проверить, устранена ли проблема.
Если вы все еще сталкиваетесь с той же проблемой даже после включения безопасности на основе виртуализации, перейдите к следующему потенциальному исправлению ниже.
Method 1: Uninstall Hyper-V in the GUI
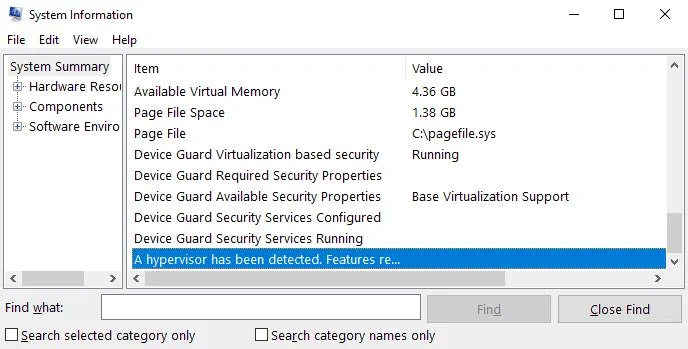
Check system information about Windows configuration by running the following command in CMD:
msinfo32.exe
A System Information window opens. On the following screenshot, you see that Hyper-V is enabled (a hypervisor has been detected), and Device Guard Virtualization-based security is running. Now you can remove these features.
You should be aware that the following Hyper-V related features will not be available after you remove Hyper-V:
- Hyper-V
- Credential Guard and Device Guard
- Virtual Machine Platform
- Windows Sandbox
- WSL2.
Remove the Hyper-V feature in the graphical user interface (GUI) by using Control Panel, Add Roles, and Features wizard.
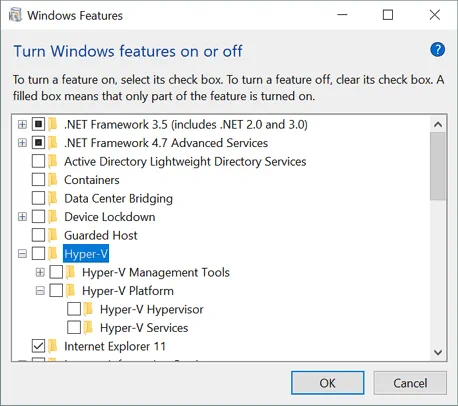
In Windows 10, open Control Panel, click Programs and Features, then click Turn Windows features on or off.
The Windows Features window opens.
Deselect the Hyper-V checkbox, and hit OK.
To finish removing Hyper-V, restart the computer.
The steps for removing Hyper-V on Windows 10 and Windows Server 2016 are similar.
In Windows Server 2016, open Server Manager and click Manage > Remove Roles and Features. In the Remove Roles and Features Wizard, go to the Server Roles step, and deselect Hyper-V. Hit Next at each step to continue. Restart is required to finish removing the Hyper-V role.
VMware Workstation and Device/Credential Guard not compatible
Based on the error message, you can see it indicates VMware Player can be run after disabling Device/Credential Guard. So, if you’re faced with this VMware Workstation and Device/Credential Guard not compatible issue on Windows 10, you can try the 2-step solution below to resolve the issue.
- Disable Hyper-V (if enabled)
- Disable the Device Guard Policy via Registry Editor
Let’s take a look at the description of each step.
1] Disable Hyper-V (if enabled)
To disable Hyper-V, do the following:
- Press Windows key + R to invoke the Run dialog.
- In the Run dialog box, type appwiz.cpl and hit Enter to open Programs and Features applet.
- In Programs and Features, on the left-hand side, click Turn Windows features on or off.
- In the Turn Windows features on or off popup that appears, uncheck Hyper-V.
- Click OK.
Hyper-V will now be disabled from your computer.
Restart the computer and on boot, proceed with Step 2.
2] Disable the Device Guard Policy via Registry Editor
Since this is a registry operation, it is recommended that you back up the registry or create a system restore point in case the procedure goes wrong. Once you have taken the necessary precautionary measures, you can proceed as follows to resolve the VMware Workstation and Device/Credential Guard not compatible issue.
- Press Windows key + R to invoke the Run dialog.
- In the Run dialog box, type regedit and hit Enter to open Registry Editor.
- Navigate or jump to the registry key path below:
Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\DeviceGuard
On the right pane, double-click the EnableVirtualizationBasedSecurity key to edit its properties.
If you don’t see the key, create it by right-clicking on a blank space on the right pane and then select New > DWORD (32-bit) Value. Rename the value name as EnableVirtualizationBasedSecurity and hit Enter.
- Input in the Value data field and hit Enter.
- Next, navigate or jump to the registry key path below:
Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa
- On the right pane, double-click the LsaCfgFlags key to edit its properties.
- Input in the Value data field and hit Enter.
You can now exit Registry Editor and restart your system.
You can be able to disable Device Guard policy using the Local Group Policy Editor, as well.
Once you have completed the procedure and restarted your computer, the VM should be running fine.
Conclusion
New Windows features such as Virtualization Based Security (Device Guard and Credential Guard), Windows Sandbox, WSL that use the Hyper-V engine cause a lot of problems to users, administrators, and software developers using other hypervisors such as VMware Workstation, VirtualBox, QEMU, and Google Android Emulator on Windows machines. There are two approaches to resolve these incompatibility issues: Disable/uninstall Hyper-V or use new versions of virtualization applications that support work with Hyper-V APIs, such as Windows Hypervisor Platform API provided by Microsoft.
Running VMs on VirtualBox, VMware Workstation, and other hypervisors on machines with Hyper-V by using APIs can degrade the performance of non-Hyper-V VMs. Data backup is crucial for the cases when virtualization applications fail. If you still haven’t chosen the best Hyper-V backup solution for your environment, consider NAKIVO Backup & Replication. The solution offers robust backup, ransomware protection, disaster recovery and more. Download the Free Edition to see the solution in action.
Как исправить ошибку VMware Workstation and Device/Credential Guard are not compatible при включении виртуальной машины.
VMware Workstation – программа виртуализации одной или нескольких операционных систем на персональном компьютере. Обычно её используют для тестирования различного софта и дистрибутивов. Но многие пользователи столкнулись с проблемой — vmware workstation ошибка при включении виртуальной машины:
VMware Workstation and Device/Credential Guard are not compatible. VMware Workstation can be run after disabling Device/Credential Guard.
Начиная с версии VMware Workstation 12.5 на Windows 10 не запускается виртуальная машина. Всё из-за защиты учётных записей, и для того чтобы виртуалка работала корректно, нужно отключить этот самый защитник.
Background and Working Principle
After you install VMware Workstation, VMware Player, or Oracle VirtualBox on a Windows machine, you might get errors when starting a VM in these virtualization applications. The errors occur even if Hyper-V VMs are not running at that time. You can install VMware Workstation and VirtualBox, and run VMware VMs and VirtualBox VMs on the same computer, but not simultaneously. What causes this problem with Hyper-V? Let’s take a closer look.
VMware Workstation, VMware Player, and VirtualBox are type 2 hypervisors, while Hyper-V is a type 1 hypervisor. A type 2 hypervisor is installed on the operating system that is running on hardware. A type 1 hypervisor is installed on top of hardware. All hypervisors require processor virtualization extensions, which are instruction sets for hardware virtualization – Intel VT-x or AMD-V. Hyper-V takes control of virtualization extensions when Windows boots. These virtualization extensions are not available for VMware Workstation and VirtualBox when Windows loads. Only one software component can use Intel VT-x or AMD-V at a time.
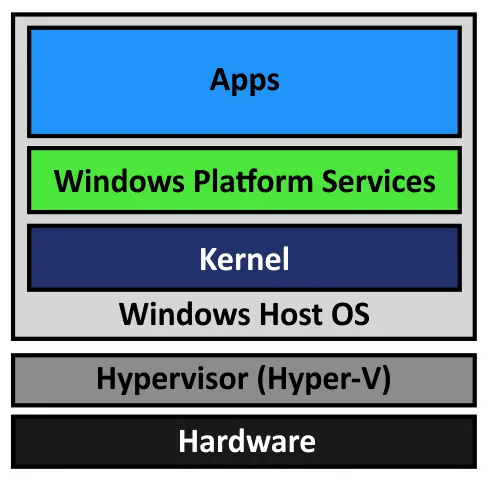
This incompatibility is caused by Hyper-V because virtualization extensions are not exposed to type 2 hypervisors installed on a Windows machine where the Hyper-V role is enabled.
VMware Workstation errors:
VMware Workstation and Hyper-V are not compatible. Remove the Hyper-V role from the system before running VMware Workstation.
VMware Workstation and Device/Credential Guard are not compatible. VMware Workstation can be run after disabling Device/Credential guard.
VirtualBox errors:
BSOD, such as BSOD with SYSTEM_SERVICE_EXCEPTION
VT-x is not available (VER_VMX_NO_VMX). E_FAIL (0x80004005).
A VirtualBox VM works too slowly and uses the paravirtualisation (emulation) mode.
The most interesting situation is when a user doesn’t install Hyper-V and still encounters one of the errors mentioned earlier when using VMware Workstation or VirtualBox. The error occurs when automatic Windows updates are enabled. With the updates (Windows 10 v1607 and the appropriate Windows Server versions starting from Windows Server 2016), some new Hyper-V-related features are installed and enabled automatically without Windows user consent. These features are Device Guard and Credential Guard. Windows updates known vulnerabilities but can add issues and destroy a working configuration. That’s why many users don’t like automatic updates.
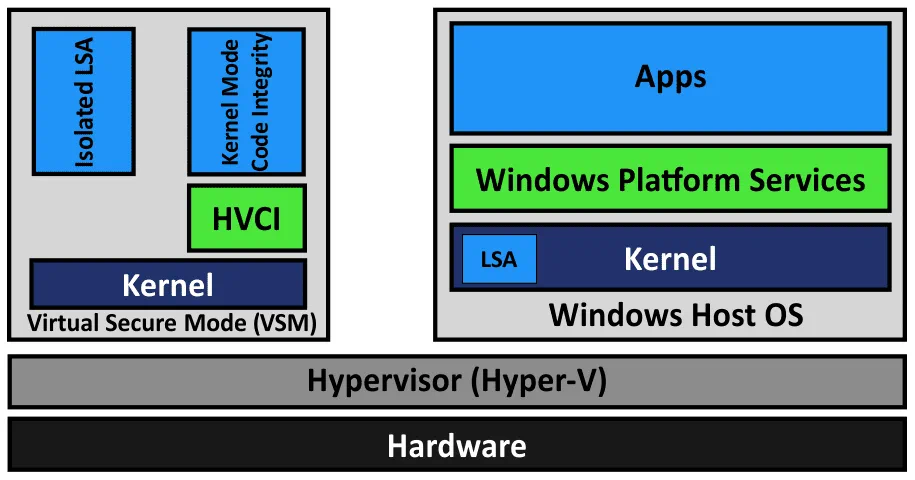
Device Guard is a group of security features in Windows. The idea of implementing this feature is to harden the execution of malicious code. Device Guard is available in Windows 10, Windows Server 2019, and Windows Server 2019. The main requirements are: UEFI running in native mode and Secure Boot enabled.
Credential Guard is a feature to minimize the impact of attacks if malicious code is already running by isolating system and user secrets to make more difficult to compromising.
Virtual Secure Mode (VSM) is a feature to leverage processor virtualization extensions that secures data in an isolated region of memory. HVCI is Hypervisor-protected code integrity. LSA is Local Security Authority.
Virtualization Based Security (VBS) is a class of technologies that uses virtualization extensions, including VSM, to provide security in Windows. The Hyper-V role is required to make these features work (Hyper-V management tools are not needed).
The hypervisor (Hyper-V) loads first, and then the operating system (Windows) loads. Hyper-V provides an abstraction layer between hardware and the operating system. A VSM allows the tagging of specific critical processes and memory used by them as they belong to a separate independent operating system controlled by Hyper-V. The principle is similar to the isolation of two VMs running on a Hyper-V host when each VM can use only the hardware resources provisioned to it.
Note: If you need a type 1 hypervisor from VMware, use VMware ESXi and VMware vSphere environment. Learn more in these blog posts: Hyper-V vs VMware, VMware Workstation vs VMware Player, and How to install ESXi on Hyper-V.
Let’s explore how to resolve the incompatibility issue of Hyper-V and other virtualization applications in detail.
Method 3: Disable Hyper-V by Using BCDedit
The idea behind this method is to edit boot configuration data and disable booting of Hyper-V without uninstalling the Hyper-V role.
Log in to PowerShell as Administrator, or run the command from an elevated command prompt to disable Hyper-V:
bcdedit /set hypervisorlaunchtype off
If you need to re-enable Hyper-V and set the default value back, run this command:
bcdedit /set hypervisorlaunchtype auto
For more control and convenience, disable fast boot in Windows 10. Open Windows Registry Editor, and go to:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Power
Set the HiberbootEnabled parameter to
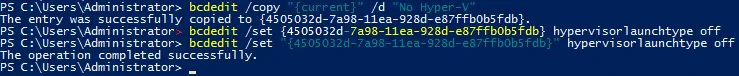
If you need to use Hyper-V VMs sometimes, create two entries for a Windows boot loader: one to boot Windows with Hyper-V and another to boot Windows without Hyper-V. Then, select the needed option before you boot Windows. This approach prevents you from running commands in PowerShell manually each time when you need to enable or disable Hyper-V.
bcdedit /copy «{current}» /d «No Hyper-V»
«The entry was successfully copied to {xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx}.»
Copy and paste your value instead of xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx.
bcdedit /set «{xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx}» hypervisorlaunchtype off
Restart the computer.
Once your computer has restarted, you should see two options in Windows Boot Manager.
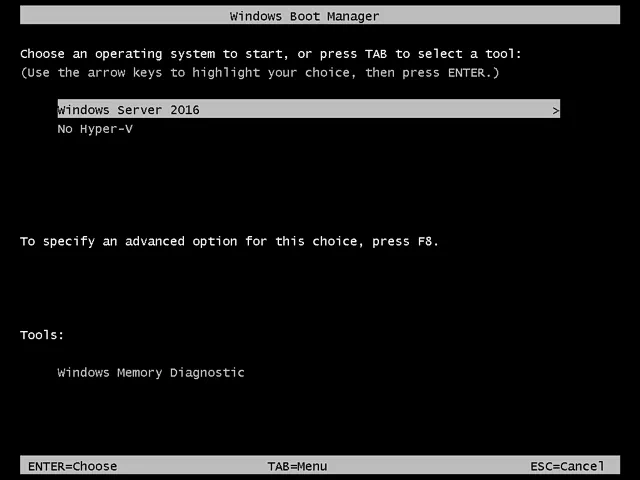
If you want to remove the No Hyper-V boot entry, use the /delete option for bcdedit.
Get a list of the current boot entries:
bcdedit /v
A list of all entries with their identifiers is displayed in the output. Copy the ID of the entry which you want to remove, and run the following command:
bcdedit /delete «{xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx}»
Method 5: Turn off virtualization Based Security in Windows
This method is used to disable Device Guard and Credential Guard, which are Hyper-V-related features.
Open the Group Policy Editor for a local machine. The group Policy Editor is available in Windows 10 Pro, Enterprise, and Education. In the command prompt, run gpedit.msc
Go to Local Computer Policy > Computer Configuration > Administrative Templates > System > Device Guard
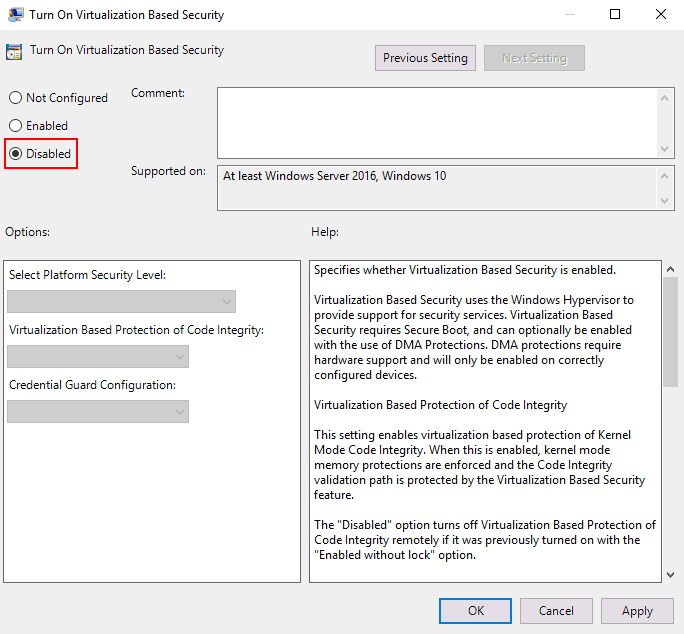
Double-click Turn On Virtualization Based Security. By default, the status of this setting is Not configured.
In the window that opens, select Disabled and hit OK to save settings, and close the window.
Edit Registry as an alternative
In Windows 10 Home, where the Group Policy Editor is not present, you can disable Virtualization Based Security in Windows Registry.
Create a backup of the Windows registry before changing registry settings to avoid errors and issues.
Open Registry Editor. Run regedit in the command line that should be opened as Administrator.
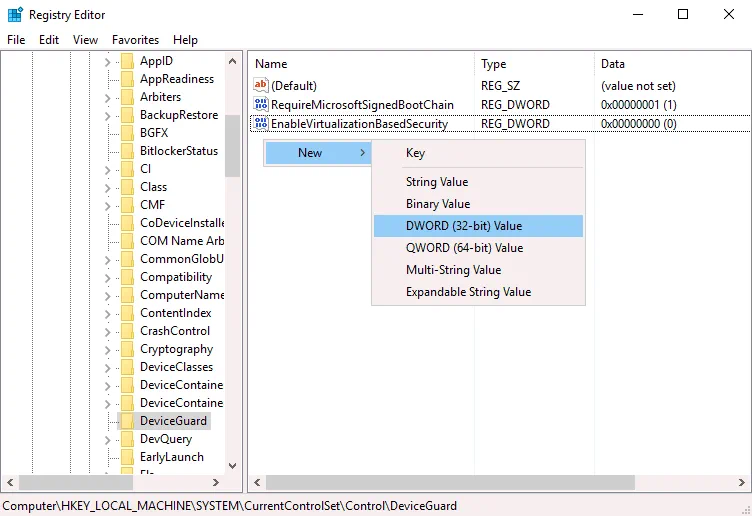
Go to HKEY_LOCAL_MACHINE > SYSTEM > CurrentControlSet > Control > DeviceGuard
Create the EnableVirtualizationBasedSecurity entry if this entry is missing. To create a new entry, right-click an empty place in the DeviceGuard directory, and in the context menu, click New > DWORD (32-bit) Value. Enter the EnableVirtualizationBasedSecurity name for this registry entry. By default, data set for this entry should be (see the following screenshot). You can double-click the EnableVirtualizationBasedSecurity and set manually.
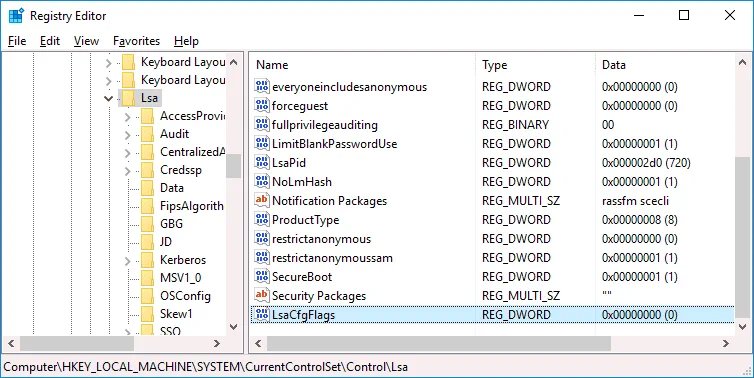
Go to HKEY_LOCAL_MACHINE > SYSTEM > CurrentControlSet > Control > Lsa
Create a new registry entry in the Lsa directory. Right-click an empty space in the right pane of the Registry Editor window. In the context menu, click New > DWORD (32-bit) Value.
Enter the LsaCfgFlags name for this value. This value must be set to .
Close the Registry Editor, and restart your computer.
You can run the following commands in PowerShell (as Administrator) to disable Device Guard and Credential Guard on the next Windows boot.
Mont a UEFI system partition to the drive X: (select an unused volume):
mountvol X: /s
Copy the C:\Windows\System32\SecConfig.efi to X:\EFI\Microsoft\Boot\SecConfig.efi with an option to overwrite the file if the file exists. This file is a boot image for Windows security configuration tool.
copy %WINDIR%\System32\SecConfig.efi X:\EFI\Microsoft\Boot\SecConfig.efi /Y
Create a new option in the boot menu with the ID {0cb3b571-2f2e-4343-a879-d86a476d7215} and the DebugTool name:
bcdedit /create {0cb3b571-2f2e-4343-a879-d86a476d7215} /d «DebugTool» /application osloader
Set the boot option you created to boot at the previous step to \EFI\Microsoft\Boot\SecConfig.efi:
bcdedit /set {0cb3b571-2f2e-4343-a879-d86a476d7215} path «\EFI\Microsoft\Boot\SecConfig.efi»
Set Windows Boot Manager to make the new entry the default one for the next reboot. After that, reboot your Windows should go back to normal boot.
bcdedit /set {bootmgr} bootsequence {0cb3b571-2f2e-4343-a879-d86a476d7215}
Set the bootloader to pass the options DISABLE-LSA-ISO,DISABLE-VBS to the SecConfig.efi file when the bootloader launches the file.
bcdedit /set {0cb3b571-2f2e-4343-a879-d86a476d7215} loadoptions DISABLE-LSA-ISO,DISABLE-VBS
Set the partition for the booted drive to the X: drive:
bcdedit /set {0cb3b571-2f2e-4343-a879-d86a476d7215} device partition=X:
Unmount the X: drive from the system:
mountvol X: /d
Файл конфигурации виртуальной машины
Итак, при запуске машины получаем ошибку открытия файла конфигурации. Следовательно, этот файл повреждён или отсутствует. В некоторых случаях ошибка может быть обусловлена недостаточным наличием прав для открытия файла.
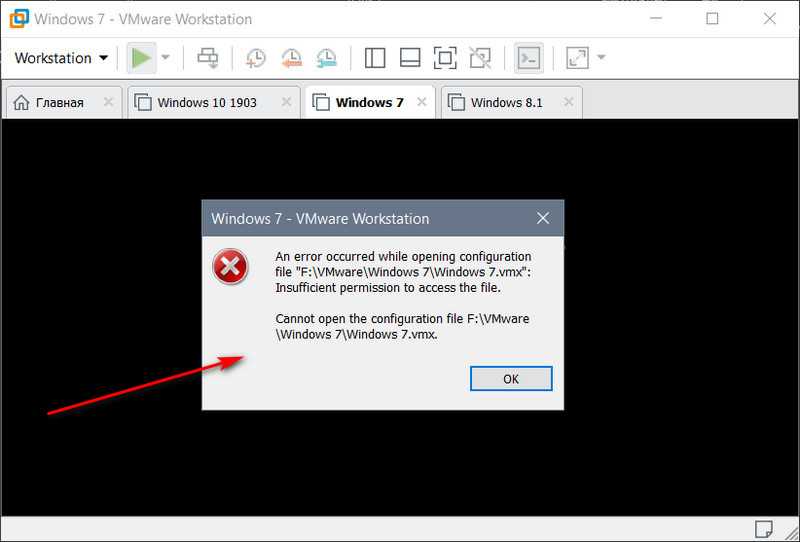
Можно попробовать запустить VMware Workstation с правами администратора, открыть машину, выключить гостевую ОС и попробовать снова запустить машину в программе без прав администратора. Если это не поможет, придётся виртуальную машину пересоздать. Но на базе её существующего виртуального диска.
Файл конфигурации машин VMware – это файл формата «.wmx» , где хранятся параметры эмуляции оборудования и прочие настройки, которые мы указываем при создании машин и потом меняем их. Файл конфигурации хранится в папке виртуальной машины, его путь прямо указан в окошке сведений.
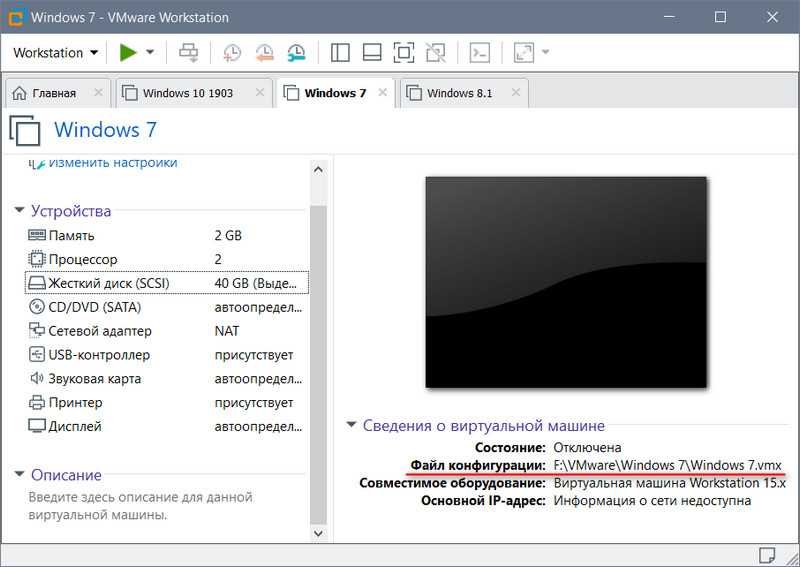
Повреждение или удаление файла конфигурации влечёт за собой невозможность работы виртуальной машины. Однако этот файл никак не влияет на содержимое виртуального диска. В последнем сохранено состояние гостевой ОС, и после пересоздания машины мы продолжим работу с этой гостевой ОС. Разве что будут утеряны какие-то данные последнего сеанса работы гостевой ОС, если у машины было приостановленное, а не выключенное состояние. Ну и также будут удалены снапшоты, если они использовались.
Method 6: Update VMware Workstation
If you have Windows 10 version 2004 (20H1) build 19041 or newer on your physical computer, you can upgrade VMware Workstation to VMware Workstation 15.5.6 or newer and run VMware VMs on your Windows machine without disabling/uninstalling Hyper-V and Virtualization Based Security (VBS) features, including Device Guard and Credential Guard.
Due to many complaints from customers, Microsoft and VMware decided to develop a joint project that adopts Microsoft Windows Hypervisor Platform (WHP) APIs to allow type 2 hypervisors, such as VMware Workstation, to run on a host where Hyper-V is enabled. These APIs allow applications to manage CPU resources, read/write registry values, terminate CPU operation, and generate interruptions.
VMware Workstation before version 15.5.5 uses a Virtual Machine Monitor (VMM) that has direct access to a CPU and virtualization instruction sets (Intel VT-x or AMD-V). A VMM operates in a privileged mode. If Virtualization Based Security features are enabled on a Windows host, then an additional hypervisor layer (Hyper-V) is added between hardware and Windows. Hyper-V has direct access to CPU features used for hardware virtualization, and VMM has no access to CPU virtualization features.
VMware made changes in the architecture of VMware Workstation 15.5.6 to allow their product to use Microsoft WHP APIs and fix the compatibility issue. VMM can now run at the user level (not in the privileged mode) using the WHP APIs and run VMs without direct access to CPU virtualization extensions. This mode is called User Level Monitor (ULM) or a Host VBS mode. If you uninstall Hyper-V-related features from your Windows host, VMware Workstation detects it automatically, and VMM is switched to direct access of CPU virtualization extensions (running in the privileged mode).
Windows Hypervisor Platform (WHP) must be installed on a physical Windows machine where Hyper-V is enabled to allow VMware Workstation to run VMware VMs on this machine. Install the Windows Hypervisor Platform feature in Control Panel by clicking Turn Windows features on or off.
Thus, you can update Windows 10 and VMware Workstation on your physical machine to versions that support running Hyper-V-related features and VMware Workstation VMs on the same machine.
Limitations of the Host VBS mode:
- Windows Hypervisor Platform is not supported on Windows Server 2016 and other Windows Server versions and editions. As a result, VMware Workstation cannot run VMs in the host VBS mode on physical machines running Windows Server.
- Nested Virtualization is not supported. You cannot run nested VMs (VMs inside VMware Workstation VMs).
- VMware VMs can run slower.
- X86 performance monitoring counters (PMC) are not supported.
- User-mode protection keys (PKU) capability is not available.
- Restricted transactional memory (RTM) and hardware lock elision (HLE) capabilities are not available.
Method 1: Disabling Hyper-V
According to various user reports, one of the most common causes that will trigger the “VMware and DeviceCredential Guard are not Compatible” error is a conflict between Hyper-V (Microsoft’s proprietary virtualization technology) and VMware. Keep in mind that both VMware and VirtualBox will pick their own virtualization technologies by default.
However, there is one Windows Update (KB4515871) that is known to force certain 3rd party applications to use Hyper-V – in VMware, this will end up producing the “VMware and DeviceCredential Guard are not Compatible” error.
If this scenario is applicable and you recently installed a Windows update that you think might be responsible for the newly appeared error, follow one of the guides below to disable Hyper-V in order to clear the way for VMware to use its own virtualization technology.
A. Disabling Hyper-V via CMD
- Open up a Run dialog box by pressing Windows key + R. Next, type ‘cmd’ inside the text box and press Ctrl + Shift + Enter to open up an elevated Command Prompt.
Note: Once you see the UAC (User Account Control), click Yes to grant admin access.
- Once you’re inside the elevated CMD prompt, type the following command and press Enter to disable the Hyper-V function on a system level:
dism.exe /Online /Disable-Feature:Microsoft-Hyper-V
- After the command is successfully processed, close the elevated Command Prompt window and reboot your computer.
- Once the next startup is complete, open VMware and repeat the action that was previously causing the error.
B. Disabling Hyper-V via Powershell
There is also another way to enable or disable Hyper-V in Windows 10. To do it, please run PowerShell as administrator and then type the following commands:
bcdedit /set hypervisorlaunchtype off (disable Hyper-V) bcdedit /set hypervisorlaunchtype on (enable Hyper-V)
C. Disabling Hyper-V via GUI
- Press Windows key + R to open up a Run dialog box. Inside the text box, type ‘appwiz.cpl’ and press Enter to open up the Programs and Features menu.
- Once you’re inside the Programs and Files menu, use the menu on the left-hand side to click on Turn Windows features on or off.
- When prompted by the UAC (User Account Control), click Yes to grant administrative privileges.
- From the insides of the Windows Features menu, expand the drop-down menu associated with the Hyper-V folder. Next, uncheck the box associated with Hyper-V Management tools and Hyper-V platform before clicking Ok to save the changes.
- Once you manage to disable Hyper-V from the GUI menu, restart your computer and see if the issue is resolved at the next computer startup.
If you still end up seeing the “VMware and DeviceCredential Guard are not Compatible” error when launching WMware Player / WMware Workshatiaon or when trying to mount a virtual machine, move down to the next potential fix below.
VMware Workstation и Device/Credential Guard несовместимы
Судя по сообщению об ошибке, вы можете видеть, что VMware Player can be run after disabling Device/Credential Guard . Итак, если вы столкнулись с этой проблемой VMware Workstation and Device/Credential Guard not compatibleWindows 10 , вы можете попробовать двухэтапное решение, описанное ниже, чтобы решить эту проблему.
- Отключить Hyper-V (если включено)
- Отключите политику Device Guard(Device Guard Policy) через редактор реестра .(Registry Editor)
Рассмотрим описание каждого шага.
1] Отключить Hyper-V (если включено)
Чтобы отключить Hyper-V , сделайте следующее:
- Нажмите клавишу Windows + R, чтобы вызвать диалоговое окно « Выполнить(Run) ».
- В диалоговом окне «Выполнить» введите appwiz.cpl и нажмите Enter, чтобы открыть апплет « Программы и компоненты ».(Programs and Features)
- В разделе « Программы(Programs) и компоненты(Features) » слева щелкните « Включение или отключение компонентов Windows».( Turn Windows features on or off.)
- В появившемся всплывающем окне « Включить или отключить функции Windows » снимите флажок (Turn Windows features on or off )Hyper-V.
- Нажмите «ОК».
Теперь Hyper-V(Hyper-V) будет отключен на вашем компьютере.
Перезагрузите компьютер и при загрузке перейдите к шагу 2(Step 2) .

































